- Be vigilant, check and challenge any requests, even if they come from someone senior.
- Treat all requests from employees that request any changes to regular account details, as suspicious.
- Contact the individual to check the request is genuine. Don’t respond to the email, instead use contact details you already hold, not those included in the request.
- Don’t make any changes to contact or payment details until you’re certain it’s genuine, even if they’re claiming it’s urgent.
- Make sure all staff are aware of this type of fraud and help them to stay vigilant, including the senior directors and CEO. Make sure staff feel able to approach senior people to verify if a request is genuine.
- Have a documented process for the arrangement of payments. Any requests outside of this process, particularly if they are by email, should be treated as suspicious until verified with the individual directly.
Overlay
What are compromised email scams?
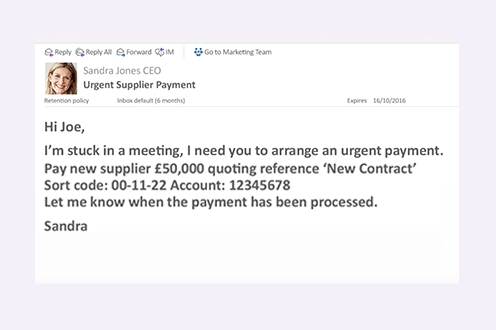
- Fraudulent emails may appear to come from senior people, such as the CEO or Finance Director within your business, requesting urgent payment.
- Fraudsters pretend to be a genuine employee and tell you their personal bank details have changed. The communication will ask you to make all future salary payments to a new fraudulent account.
- Fraudsters may also pretend to be clients, employees and supply chain partners.
- There are several ways for attackers to get access to a legitimate mailbox, so they can send these fake emails. Tactics include a password spray, an attack that attempts to access many accounts with a few commonly used passwords, or the use of malware and phishing.
- Successful attacks allow fraudsters to intercept emails between two parties by accessing the company’s account or impersonating a client or other firm.
- The purpose of these scams is to look as if they come from a genuine sender. When the customer pays the invoice, the money goes straight to the fraudster’s account. Common examples of this scam:
- A fake invoice from a supplier asking for payment
- An email connected to a sale of a property, which requests the proceeds of sales funds to be paid to a ‘new’ account.
- An email from an executive asking an employee to make an urgent payment.
- An email from an employee asking for their salary to be paid to a ‘new’ account.
- A fake invoice from a supplier asking for payment
What to look out for

Take Five to stop fraud
Take Five is a national campaign that offers straight-forward and impartial advice to help everyone protect themselves from preventable financial fraud. This includes email deception and phone-based scams as well as online fraud – particularly where criminals impersonate trusted organisations.
